Table of Contents
As a regular internet user, you have many accounts with different levels of importance. Think about the process of signing into these accounts. You might have noticed that you must prove you are the user for an account to give you access.
The method of establishing your identity on the website is called authentication.
Different types of accounts have different levels of authentication requirements. One thing people need to realize is that the choice of the kind of authentication method can make or break your online security.
Are you curious about how to improve your online security using better authentication? Then, this article is for you.
What Is Authentication?
When an online platform wants to give you access, it must first prove you are the right person. This is the authentication process.
Authentication starts like a simple knock-knock joke. The website first asks who you are. You then prove your identity in one way as the website checks its records. If the records match, then you are granted access. If they don’t, you have to try again.
Why Should You Think About Authentication?
Cyber security has become a big deal nowadays. As many people continue joining the Internet, so do the criminals improve their tactics for accessing private information.
Statistics indicate that the levels of cybercrime have risen by at least 69% since 2015. Anyone who wants to stay safe online must develop strategies for keeping everything they do secure.
One of the best strategies for increasing security in online interactions is having suitable authentication methods.
Through authentication, you can limit the kind of people with access to private data to only those authorized. Maintaining the best authentication methods falls on both the online platform and the users.
As we shall discuss below, the different authentication methods give all stakeholders different responsibilities.
Types Of Authentication Methods
There are different kinds of authentication methods, ranging from the simple ones to the most sophisticated ones. The authentication method you choose depends on what kind of data you want to keep safe.
Highly confidential information, such as government records, needs highly-secure authentication. On the other hand, general information that is on the public platform can work with simple authentication methods.
Here are a few options you can choose from as you decide which authentication method will work for your online platform:
- Passwords
- Biometrics
- Multi-factor authentication
1. Best Practices On Passwords
Nearly everyone has interacted with passwords as an authentication method. The simple function behind password authentication is the user inputs the password as the online platform checks its records for a match. The user will only be allowed to proceed if the password matches.
Password hacking is one of the leading causes of cyber security threats online. Never reuse the same password for different accounts to strengthen your online security using password authentication.
Reusing passwords is a significant security risk, with at least 51% of all passwords online being reused. To stay secure, have a unique password for every account.
Additionally, ensure that your passwords are not related to your username or any ordinary English words. Always use capital letters, small letters, numbers, and special characters in your passwords.
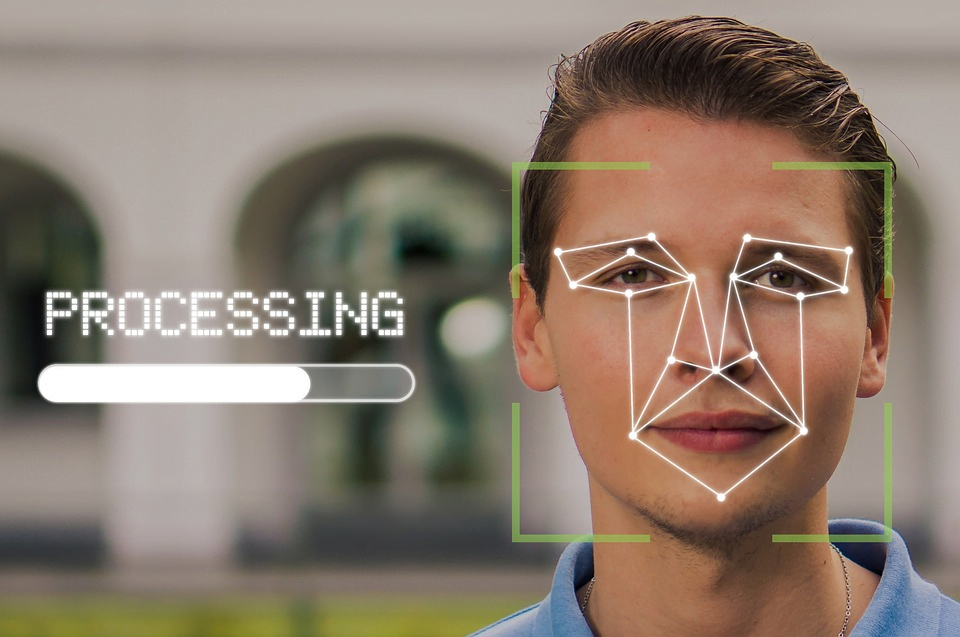
2. Best Practices On Biometric Authentication
Biometric authentication allows you to use different parts of your body to authenticate your identity. Some of the most commonly used elements of biometric authentication include:
- Iris
- Facial recognition
- Fingerprint scanning
- Voice recognition
As you would expect, not all kinds of devices support all types of biometric authentication. Fingerprint, facial recognition, and iris scanning are popular on mobile phones and computers. Voice recognition is more sophisticated and is unlikely to be used in online security.
3. Multi-Factor Authentication
Multi-factor authentication allows users to provide different layers of security to protect their accounts online. A typical multiple-factor authentication asks the user to provide different authentication methods for access. Standard multi-factor authentication methods include asking a user to provide the following:
- Something they know (passwords or answers to security questions)
- Something they have (like passwords or a one-time password to a phone)
- Something they are (like biometrics)
Multi-factor authentication is ideal for people intending to have the ultimate security on their devices and accounts. If anyone gets access to any authentication method, your security is still guaranteed since they are unlikely to get all of them.
In some instances, multi-factor authentication can include a time limit to prevent hackers from gaining access to any authentication method.
Final Words
In a world where everything happens online, getting a strong online security system can determine many things. Through proper authentication methods, you can increase your security and maintain the safety of your private information.
Understandably, many authentication methods can bother you when you only want to check your social media. However, updating your online authentication methods can make or break your safety. Remember to incorporate biometrics any time you sign in, as biometric information